G-Suite End-Users Hardened Against Phishing Attacks with BIMI
Google is implementing the BIMI standard to help protect G-Suite users from spam and fraud, and to help filter phishing attacks.
Phishing attacks are emails that attempt to trick the user to click on a hyperlink to access a system they shouldn’t. In order to convince the user to click, hackers will often include the business logos of trusted brands to bestow a feeling of legitimacy and importance.
On July 21, 2020, Google announced a new security feature that’ll be rolled-out to G-Suite users to help protect them from these kinds of attacks.
The feature implements an emergent email standard called Brand Indicators for Message Identification (BIMI) and its function is to uniquely verify the use of corporate logos using the DMARC system - the same system that’s used to validate the authenticity of an email sender.
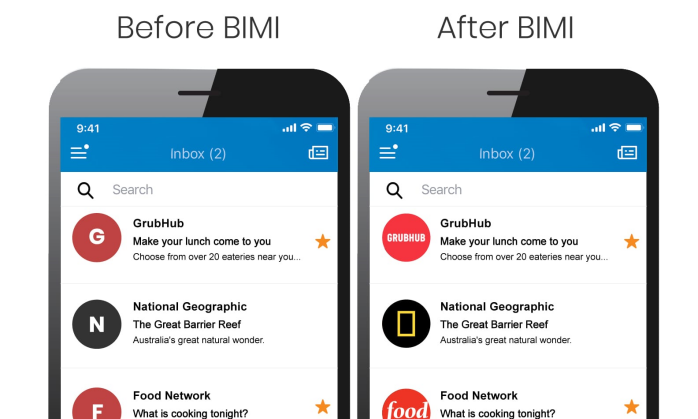
Emails delivered to Google’s mail system are scanned for fraud and abuse. Under BIMI, a registered brand logo will be validated and presented to the G-Suite end user in the round avatar slot aside an email. It’s a visual cue that both re-affirms brand-trust and indicates safety to the end user.
Messages that fail validation for the use of a corporate logo are filtered from the end user.
The technical side of BIMI requires email senders to:
use SPF and DKIM, and to publish a specific DMARK enforcement policy for the domain of either “p=quarantine” or “p=reject”.
register their logo with the BIMI working group and publish a BIMI record;
acquire a Verified Mark Certificate for their logo (a Google-specific requirement currently offered by only Entrust, DataCard, and DigiCert).
All of these controls benefit the G-Suite user as fraudulent use of corporate logos would potentially be filtered, making their use within spam and phishing attacks useless.
Google intends to implement this feature (and many others related to mail safety) over the next year.
The Perils of Private Email Accounts
This small business owner was shocked when I had to tell him of a potential information breach ... because he relied upon private email solutions for his business. Here's why that's a bad idea.
Uh Oh, Spaghetti-o ...
A client approached me the other day with a concern.
He feared that an employee that recently left the company was poaching his client base. He needed me to make sure that his systems were secure. I confirmed that was the case, but then he asked, "What about her email?"
Prior to engaging me, the client just had his employees setup private Yahoo! accounts. Now, with the employee gone, he needed to take control of that data.
And Now ... The Bad News ...
"No-can-do," I had to tell him, and I needed to explain some rules of the road.
Yahoo! is a private email container. As an employer of the employee, he can't access it nor control it; the EULA (End User License Agreement) is between the provider and his employee. FCC rules say that's private property, and, attempting to monitor what goes on in those email accounts is tantamount to eavesdropping on your employees.
"But those are my clients," he argued, and I empathized, but I suggested there's little he can do.
"You shouldn't have been relying on private email accounts for company business," I suggested.
And then I had to explain the really bad part.
Classified Data
You see, this guy is in the business of working with confidential, classified forms of Protected Health Information, or, PHI. Every now and again, PHI about his customers were probably emailed to this individual and fell outside of his control. Further, it was possible that customer's drivers license information was shared with the former employee.
"Technically, that's potentially a breach," I had to explain, "where you've lost control of classified forms of data under two sets of law: HIPAA - federal law managing PHI - and State of Washington Data Breach Law. You've lost control of the data and can't account for its whereabouts, access control, or destruction."
So What Do We Do Now?
At that point, he started looking at me pretty nervous-like, and I discussed his options going forward.
- The company should set up a secure email and storage system. It just so happens that I'm a reseller for Google Apps. Google Apps has sought and received FISMA, ISO 27001, and SSAE 16 certifications for information system security, and understands its Business Associate obligations for managing PHI. Google's server traffic is encrypted and the data stored on its cloud platform is encrypted; Google Apps Privacy and Security are some of the best practices in the industry. Google's a big proponent of responsible computing and that's why I work with them.
- Under the company's flag, they own this asset. They can control and audit and revoke access. They can determine who and what devices receive confidential forms of information that they're responsible for. And if a termination event happens again, we're in control.
- Implement an Administrative Control (a policy) that states employees can only use the corporate email system for company business. Violating that policy is grounds for dismissal. That sets up management's intention and clarifies the obligations of employees. That's called an Acceptable Use Policy, and it turns out that I've got a stock policy just hanging around that he could modify.
- Finally, we train the employees on handling classified forms of information, and advise them of their responsibilities and tips for best practices.
In this way, I helped him craft a more successful strategy going forward that would limit his liability, protect the interest of his customers, and bring him closer to a state of information compliance.
That's the kind of value I bring to every engagement with my customers. Want to know more? Give me a jingle - I'd be happy to talk about how I can help you.
R
Heartbleed Vulnerability Advisory
Russell Mickler, technology consultant, warns about the heartbleed bug.
This week, a doozy of a security risk was revealed concerning the way data is encrypted between computers and web servers on the Internet.
It's called Heartbleed and you may have heard of it by now.
If you are a client of mine - and as it is my obligation as your technical administrator - I wanted to take a minute to address my services and your exposure to this vulnerability.
Microsoft Windows Terminal Services
If you receive terminal service/remote desktop solutions from me, your services are ran on Microsoft Windows 2008 R2 servers. Inasmuch, Microsoft has confirmed that their platforms are not affected by the Heartbleed vulnerability so your site and its data and your communications between them are not subject to this risk.
Google Apps
If I manage your Google Apps environment, as of Thursday April 10, 2014, Google confirmed that they've patched all of their servers for their major services, so your mail, contacts, calendars, and so on - stuff I manage for you under Google Apps - are also secure:
http://www.engadget.com/2014/04/09/google-heartbleed-patch-info/
Online Backup
If you receive an online backup product from me, I've received a verbal confirmation from the vendor that their solutions are not subject to this vulnerability.
VOIP Phone Solutions
If you receive your VOIP solutions from me, I've received verbal confirmation from the vendor that their solutions are not subject to this vulnerability.
Third Party Website Hosts and Operators
You need only be concerned about this vulnerability if your website conducts any form of secure transaction, such as logins, taking payments, or processing orders.
If your website just serves-up webpages with information, you are not affected by Heartbleed. If your website takes in any information securely, it is likely subject to this vulnerability.
If your website or email service or backup service is hosted by a third party, it is their responsibility to patch their servers and advise you of their status. I recommend you contact them immediately for a status.
Third Party Cloud-Based Services
Nearly all websites are affected by the Heartbleed vulnerability including popular brands like Netflix, Dropbox, Twitter, Facebook, large banking institutions, and the like. The situation right now is rather fluid and broad but I'd recommend the following approach:
1. Take an inventory of the 3rd party websites that are related to your business and that you frequent; ie, your financial institution, online business software, file sharing software, and so on.
2. Visit their websites or blogs for the latest update/information about their vulnerability to Heartbleed.
3. Following their confirmation that their vulnerability has been addressed, you would want to change your password with that service at the earliest opportunity.
Android Phones
Finally, Google has confirmed that some versions of the Android (Droid) operating system are exposed to this vulnerability. The models and versions vary. Those who run Android/Droid operating systems on their phones will want to apply updates throughout the weekend or discuss this matter with their cell phone carrier/provider. To test whether or not your Android phone is vulnerable, you may wish to try this solution.
If you have any questions or concerns, please feel free to contact me.
R