Top Cybersecurity Risks to Small Businesses: How They Impact Operations, Employees, and Consumers
Cyberattacks are a growing threat to small businesses, disrupting operations, stressing employees, and shaking consumer trust. Stay vigilant!
Cybersecurity threats are a growing concern for small businesses. Here are the top risks and their potential impacts:
Phishing Attacks: Phishing emails are one of the most common threats. They trick employees into providing sensitive information or clicking on malicious links. According to a 2023 report by Verizon, 36% of data breaches involved phishing. This can lead to unauthorized access to company data, financial losses, and damaged reputation.
Ransomware: Ransomware attacks can cripple business operations by encrypting essential data and demanding a ransom for its release. The FBI reported a 62% increase in ransomware incidents in 2022. This can halt business activities, leading to significant downtime and financial losses.
Insider Threats: Whether malicious or accidental, insider threats pose a serious risk. Employees with access to sensitive data can leak or misuse information. This can result in legal repercussions and loss of customer trust.
Weak Passwords: Using weak or reused passwords can make it easy for cybercriminals to gain access to systems. A study by NordPass found that 73% of passwords are duplicates. This can compromise the security of multiple accounts and sensitive information.
Software Vulnerabilities: Failing to update software regularly can leave systems vulnerable to attacks. Cybercriminals exploit outdated software to infiltrate networks. Regular updates and patches are crucial to maintaining security.
Impact on Business Operations: Cyberattacks can disrupt daily operations, cause financial losses, and damage the business's reputation. Recovery can be time-consuming and costly.
Impact on Employees: Employees may face stress and uncertainty during and after an attack. They may also be targeted directly, leading to a loss of productivity and morale.
Impact on Consumer Behavior: Customers may lose trust in a business that has experienced a data breach. This can lead to decreased sales and a tarnished reputation.
Stay Vigilant: Implementing strong cybersecurity measures, educating employees, and staying updated on the latest threats are essential steps to protect your small business.
R
Understanding Browser Hijacking
Browser hijacking poses a real threat to small businesses, leading to data breaches, financial loss, and damaged reputation.
Small businesses thrive by leveraging the Internet for operations, marketing, and communication. However, this dependency exposes them to cybersecurity threats, including browser hijacking.
Browser hijacking occurs when unauthorized software alters how your web browser operates without your consent, often redirecting you to malicious websites, changing your homepage, or inserting unwanted ads. For a small business, this can mean more than just a nuisance; it can lead to data breaches, financial loss, and damaged reputation.
A great example is when a browser is hijacked to display a fictitious message about a computer’s security. This is a great example of scareware:
Its warning is contained within the confines of the browser window.
It’s big and scary.
It includes an immediate, irrational call-to-action to dial a telephone number.
Sometimes, it may be difficult to close this window.
Recent studies show that browser hijacking has become increasingly sophisticated, with attackers using it as a gateway to deploy further malware or to steal sensitive information directly. The risk is heightened for small businesses that may not have the robust cybersecurity defenses of larger corporations. According to the Cybersecurity and Infrastructure Security Agency (CISA), small businesses are the target of 43% of cyber-attacks, many of which begin with seemingly benign browser hijacking.
The biggest risk, of course, is that somebody actually calls the number. If you ever see something like this, use Task Manager in Windows to kill the browser, or, restart your PC. Your machine’s not harmed — they’re just trying to trick you into believing it is so you’ll call that number — leading to criminal fraud. Heck, just send me a screenshot in email and I’ll give you some practical advice for getting rid of it.
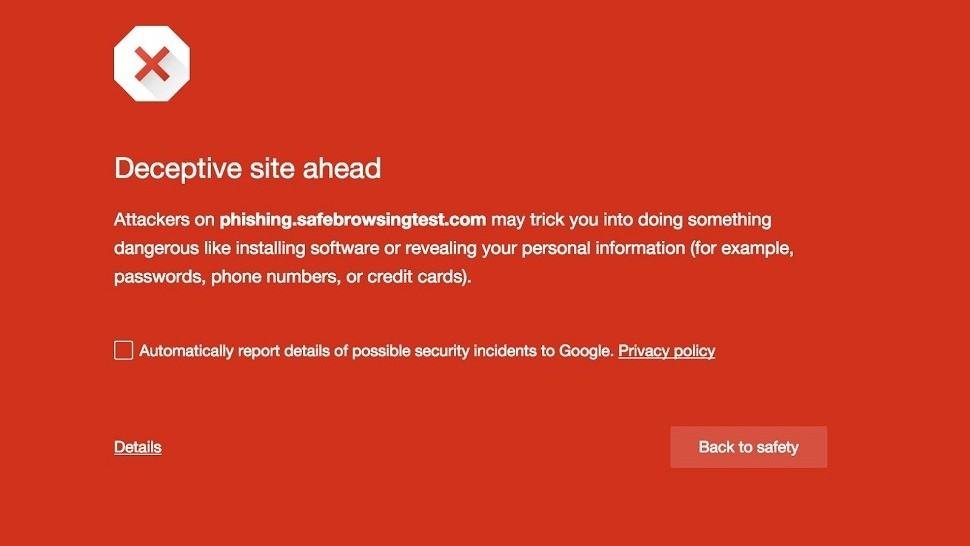
Luckily, Google is on the forefront of protecting users. Chrome can help detect when a user is going to a known-bad site and intercept the hijack with a warning that looks something like this.
The impact on small businesses can be severe. A hijacked browser can redirect customers away from your site, eroding trust and reducing sales. More alarmingly, it can be used to gather sensitive information, such as login credentials and financial data, leading to financial theft or identity theft. The recovery from such attacks involves immediate IT costs, potential legal fees, fines, and long-term brand damage.
To protect your business, it's essential to educate your team on recognizing and avoiding suspicious links and attachments, maintain up-to-date antivirus software, and regularly back up critical data. Implementing strong, unique passwords and multi-factor authentication can also add an extra layer of security.
In conclusion, the threat of browser hijacking is real and potent, especially for small businesses. By understanding the risks and taking proactive steps to mitigate them, businesses can safeguard their operations, protect their customers, and secure their future in the digital marketplace.
Beware of Email Spoofing: Your Guide to Understanding and Prevention
Discover how to protect yourself from email spoofing with essential tips and local IT support in Vancouver, WA. Stay safe online!
Email spoofing is a cyber trick you might not be aware of, but it's essential to understand to protect yourself. This deceptive practice is like a digital masquerade where scammers disguise their identity in an email, pretending to be someone you trust, like a friend, your bank, or even a coworker.
Why should this concern you? Imagine receiving an email from your bank asking for sensitive information or from a friend linking you to a strange website. It looks legitimate, but it's actually a scammer in disguise, aiming to steal your information or infect your computer with harmful software.
You may find this overwhelming, don't worry! Local IT support and computer consultants can help. They can provide the tools and knowledge to safeguard your inbox, ensuring that you can spot and avoid these deceitful emails.
Here are quick tips to protect yourself:
Always verify the sender's email address.
Be cautious with emails demanding urgent action or sensitive information.
Use email filters and security software recommended by IT experts.
Remember, staying informed and cautious can significantly reduce your risk of falling victim to email spoofing. If in doubt, contact a trusted IT consultant in Vancouver, WA, to help.
R
#EmailSafety #ITSupport #CyberSecurityTips