What is Google Drive File Stream?
A brief explainer covering what Google Drive File Stream is and how it can be used by G-Suite users to quickly access their Google Drive from a Mac or PC.
Google Drive File Stream is software developed and maintained by Google that is downloaded and installed on a target computer. When Google has updates this software, updates are pushed to existing installations and the computer is automatically updated.
Google Drive File Stream is a file system redirector. It creates a virtual disk drive on a PC or Mac. Once installed, File Stream is used to allow Google G-Suite users an easy way to access their Google Drive through their own operating system as if it were a local disk drive.
This product is only available to G-Suite users; regular non-commercial Google users use Google Drive Backup and Sync.
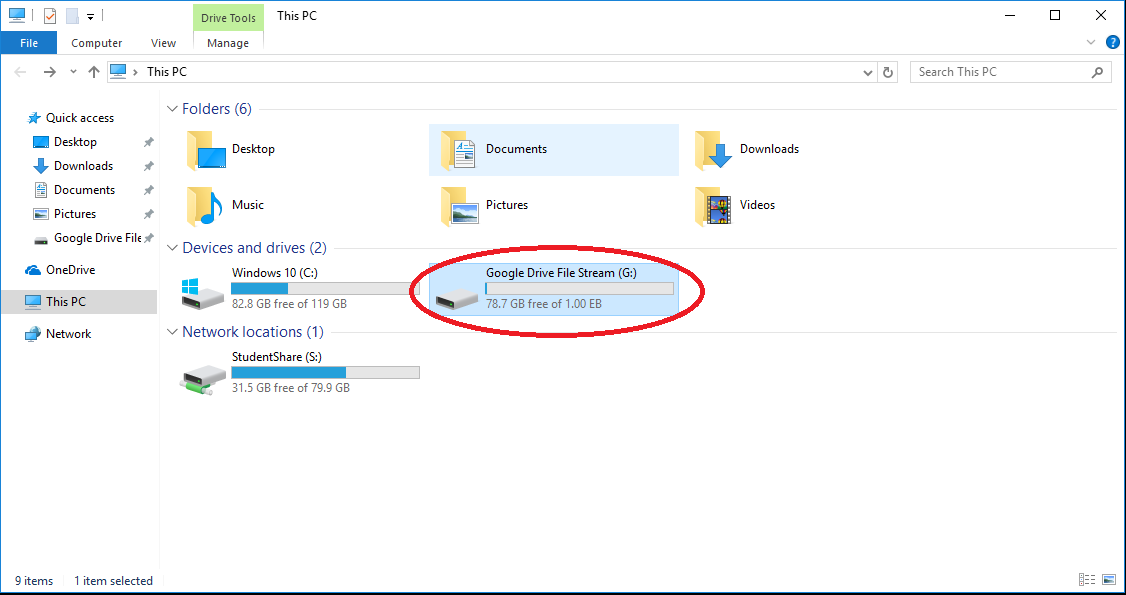
When installed on a Windows computer, the redirector attempts to map a local drive G: but it will use the next available drive letter if necessary.
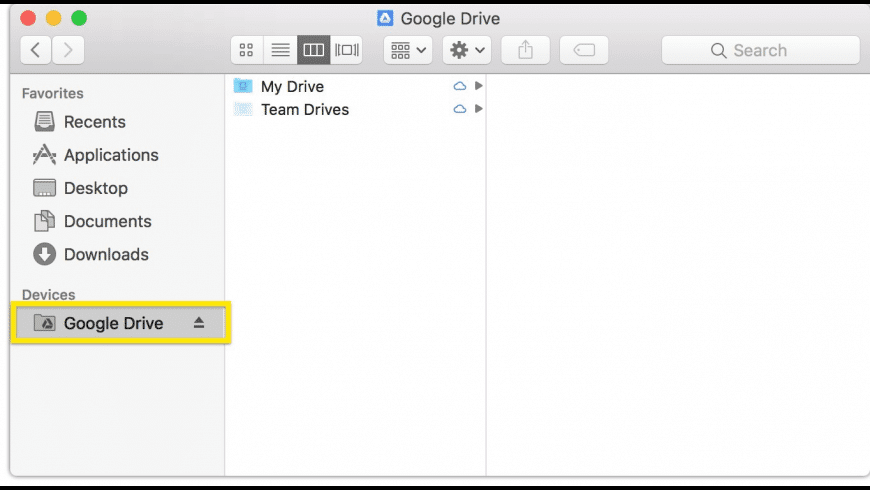
On a Mac computer, the redirector creates a separate Device under the Finder’s Device listing which can be navigated within Finder.
File Stream brings enterprise-level controls to cloud-based storage. It simplifies the use of Google Drive by making it appear like a normal disk drive in the user’s operating system, increasing the likelihood of adoption.
Instead of having the user navigate files via the web browser, the use can just drag and drop files like they normally would with any other disk drive.
Local applications like Word and Excel work seamlessly with Google Drive because those applications just see the Google Drive as another disk drive.
File Stream isn’t necessary on a Chromebook or Chromebox because its features are automatically built-in through its Files App. When a Chromebook user accesses their files, the Chromebook is already redirecting to their Google Drive and is navigable by the user.
Furthermore, File Stream isn’t offered as a product for mobile platforms like Android or iOS because the Google Drive App fulfills that function.
Helpful Videos:
Related Articles:
What is the Difference Between Google Drive File Stream and Google Drive Backup and Sync?
How Does Google Drive File Stream Work?
Is Google Drive File Stream Safe?
The Problem of File Contention with Google Drive File Stream
When You Wouldn’t Want to Use Google Drive File Stream
Ransomware Disaster Recovery for Professionals: Attorneys, Doctors, CPAs, Financial Advisors
Professional roles like attorneys, doctors, CPAs, and financial planners have a responsibility to plan for ransomware attacks and to protect the data of their clients. Here's an IT strategy that could help.
I wanted to take a few minutes to explain how business professionals - Consultants, Attorneys, Doctors, CPA's, and Financial Analysts specifically - can prepare their practice to recover from a cryptoware attack made against their data processing systems.
I'm signaling-out these professionals because they usually have non-disclosure, fiduciary obligations, confidentiality agreements, or legal mandates to safeguard their clients' data.
The nature and risk of that data is therefore more consequential than most; extra precautions should be exercised both protect data from unauthorized disclosure as well as restore operations.
This write-up may get a bit lengthy and for that I must apologize, still, I think it's a good blueprint to help draft a roadmap for your firm.
I'll be writing it in pieces over the next week and I'll provide hyperlink updates within this post to the latest posts that I complete.
Guiding Principles
We Do Not Pay Ransoms. A terrible strategy that only promotes more attacks. People who weaponize your data processing systems shouldn't be compensated.
Invulnerability Isn't Possible; Failure Is Inevitable. There's no way to guarantee absolute computer security or to avoid systems failure. It will happen. The risk must be planned for.
Disasters are Disasters. Planning for a ransomware attack is just the same as planning for an earthquake, a flood, or a fire. Our disaster recovery plan may be universally-applied.
Access Control. Only authorized people should have access to confidential information. That means strong authentication, managed risk, and low attack profiles.
Separation of Systems. We will design systems that are independent of each other and quarantine sections of risk so that firewalls exist between computing environments.
Layers of Recovery Options. Instead of depending on just one data recovery option, we will use many options to give us an opportunity to recover from a disaster.
Leverage Encryption Everywhere. Throughout our data ecosystem, we will leverage encryption wherever possible to prevent what could be compromised from being used.
Asset Management and Maintenance. A good best-practice that keeps our firm on-top of emergent threats.
Please feel free to contact me if you have any questions about what you're reading in this series.
If you have concerns about your own practice and your disaster recovery planning, contact me. I'd be happy to help.
R
Addressing Friction - Kauffman FastTrac Facilitator Presentation
A presentation on workflow analysis and systems process improvement - how to use technology to improve workflow and improve speed, accuracy, and reliability.
Today, I’m delivering a presentation on process improvement and workflow analysis.
Here are the presentation materials.